Embarking on the journey to SOC 2 compliance marks a significant milestone for any organization, signalling a commitment to robust security practices and meeting the standards demanded by the industry. At UpSlide, this achievement wasn’t about ticking boxes but instead about fostering long-term trust with our financial services clients.
Throughout this blog, I’ll share our experience in becoming SOC 2 compliant, offering insights into the why, the how, and the lessons learned. I’ve also built an easy SOC 2 compliance checklist to help other organizations, offering guidance on selecting the right compliance platform, assessing internal readiness, and making informed choices regarding audit types.
What Is SOC 2 Compliance?
SOC 2, or Service Organization Control Type 2, is a compliance framework developed by the American Institute of Certified Public Accountants (AICPA) to ensure third-party service providers store and process client data securely.
SOC 2 compliance serves as a testament to an organization’s strong security practices, commitment to upholding industry best practices, and dedication to protecting the interests of its clients and stakeholders.
Security Practices At UpSlide
At UpSlide, security has always been a key principle when designing our product and processes. We ensure sensitive data is only stored in your infrastructure, run regular audits and vulnerability scans, and use state-of-the-art processes and technology.
As our company grew and so did our clients’ expectations and requirements, we had to undertake more due diligence and security assessments. This experience prompted us to recognize areas for improvement within our company and raised many important questions:
- How can we write meaningful and compliant security policies?
- How can we continue to ensure trust between our clients and us?
- How can we better position ourselves to handle enterprise rollouts?
In 2019, we decided to bolster our security practices by:
Formally Writing New Policies, Including:
- General security policy
- Data protection and management policy
- Business continuity and management policy
- Incident response plans
- Vulnerability management program
Supporting Our Team With Relevant Tools:
- Mobile device management (MDM) solution to remotely manage all devices
- Endpoint detection and response (EDR) for all devices
- Vulnerability scan engine on our infrastructure
- Static code analysis
Why Did We Pursue SOC 2 Compliance?
We’re constantly working on improving these initial policies and programs to ensure our clients remain happy and confident in our security practices.
You might be thinking: “Why embark on a journey to SOC 2 compliance if you have strong security practices and your clients are happy with it?”
The answer is simple: we wanted to go above and beyond for our clients, remain industry-standard and offer the best product, support, infrastructure, and security measures.
Plus, conducting a third-party audit of our security program and posture wasn’t optional anymore; it is a requirement. So, at the end of 2022, we started our journey to SOC 2 compliance.

We always strive to go above and beyond for our clients, get ahead of industry-standard and offer the best product, support, infrastructure, and security measures.

Julien Villemonteix
UpSlide CEO
Common Misconceptions of a SOC 2 Audit
#1 It won’t absolve you from future security assessments
Achieving SOC 2, ISO 27001, or any other standards does not mean that you won’t have to answer security assessments in the future. However, it might mean that you have fewer intensive assessments to go through. Plus, clients can always request you complete their custom-made assessments, which you’ll need to honor.
#2 It’s not a permanent achievement, and you will need to renew it
You have to renew your SOC 2 compliant label on a yearly basis. Your ISO27001 certification can last up to three years, but you’ll still face smaller audits each year.
#3 SOC 2 is not a certification
Many companies claim that they are SOC 2 “certified”, but it’s a misconception.
The correct terminology is SOC 2 compliant – which means that an auditor reviewed your compliance with the SOC 2 standard. If you’re going the ISO 27001 route, it is indeed a certification, and you can confidently say that you are certified.
#4 It only impacts your security or IT teams
SOC 2, ISO 27001 or any security certifications impact your whole company. Throughout the audit, you’ll need to seek support from other teams, such as your:
- Legal team to review and validate policies.
- HR team to conduct changes that will make you compliant, for example, background checks.
- Development and IT teams to provide evidence that your auditor will review.
- C-suite and management teams to ensure that your project is widely adopted.
Achieving SOC 2 compliance is a team effort, so I recommend involving all internal stakeholders as soon as you start the project.
UpSlide’s SOC 2 Compliance Checklist
#1 Choose a robust compliance platform
As a medium-sized SaaS business, we don’t have fifteen people in our compliance team, so we needed to rely on tools to help us become SOC 2 compliant. We searched for tools that would:
- Integrate with our existing tech stack (Azure DevOps, Microsoft Intune, Entra ID, Trello, and Notion) for automatic evidence collection
- Monitor the status of our SOC 2 compliance
- Help us centrally store our policies
- Onboard internal teams for security training, background checks, etc.
- Connect us with auditors
- Provide a dedicated point of contact to help us with compliance questions.
We decided to go with Drata as they were the platform with the best price-to-integration ratio during our benchmark.
You’ll want to find a solution that enables you to spend more time on meaningful actions rather than evidence collection; based on our experience, we had 75% of our evidence automatically collected.
#2 Assess internal processes and identify gaps
We were quietly confident that, thanks to the maturity of our existing cybersecurity program, we were close to SOC 2 compliance. We used Drata to gain a comprehensive view of all the gaps we needed to fill to reach SOC 2.
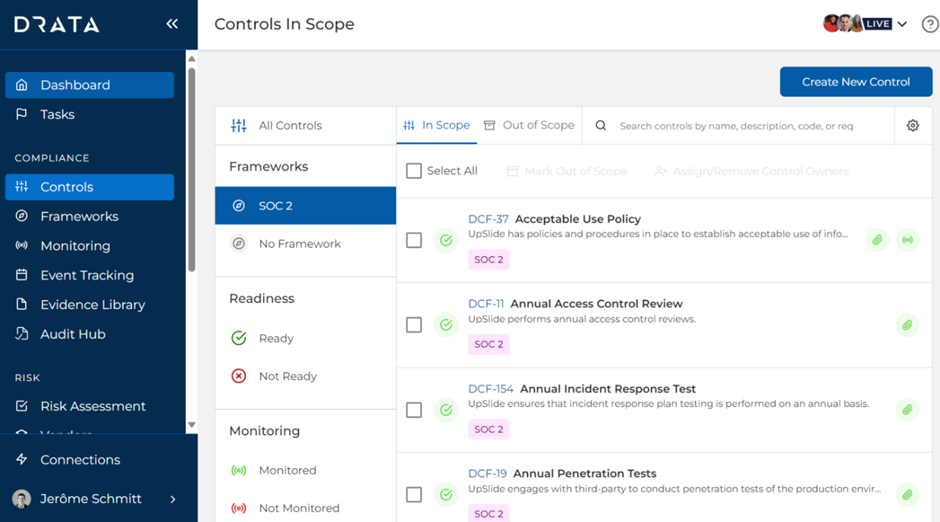
Based on this insight, we mapped out our initial tasks:
- Connect integrations for automatic monitoring and evidence collection.
- Provide our existing policies, then build new ones with the templates provided.
- Upload first unmonitored control evidence, for example, pentest and vulnerability scan results.
Gaining clarity over your gaps to address makes it easier to set tasks and achieve SOC 2 compliance.
#3 Decide SOC 1 vs SOC 2
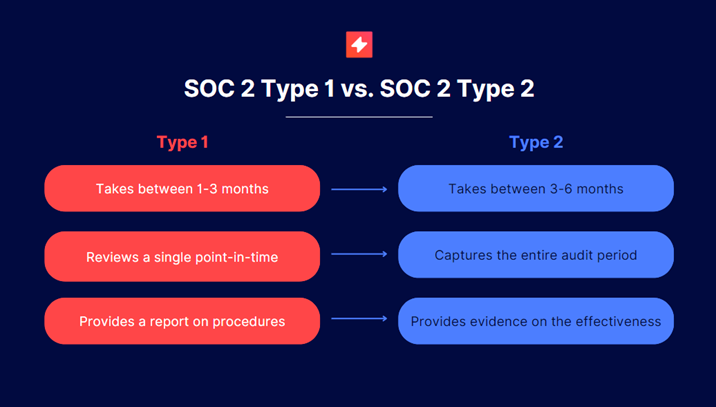
Once we were confident that our security program was in line with SOC 2, we asked ourselves: do we go for SOC 2 Type 1 or SOC 2 Type 2? Here is the difference between the two:
SOC 2 Type 1:
SOC 2 Type 1 is a point-in-time audit where the auditor checks your current compliance with SOC 2:
- Pros: It is quicker to achieve and is a good way to check if your existing security program is compliant.
- Cons: It will quickly become outdated, and you may be required to undertake a Type 2 audit anyway.
SOC 2 Type 2:
A SOC 2 audit usually takes between 3 to 6 months. SOC 2 isn’t based on a certain point in time and is reflective of your general security status as a company.
- Pros: It’s a much more credible label that your clients will trust.
- Cons: It will require more hands-on involvement, and you’ll continually have to monitor practices to ensure you remain compliant.
At UpSlide, we chose SOC 2 Type 2 because it reflects our long-term commitment to employing robust security practices.
SOC 2 Compliance Requirements
The industry standard is to conduct a six-month audit period, but due to other commitments, we decided to go with a three-month audit period for the first year.
Here’s what a SOC 2 audit period looks like:
We started our SOC 2 audit in a great position, as we had:
- Already drafted our policies and had them signed by relevant parties, such as our employees and management teams.
- Reached a compliance status of 100%.
- Built a routine of constantly monitoring our compliance.
The first key step is to find an auditor, and after discussions with our compliance partner, we decided on Sensiba.
While they’re conducting the audit, you must continuously monitor and fix compliance gaps that may occur, such as disk encryption that fails on a specific device or multi-factor authentication (MFA) not properly detected for a user account.
We recommend manually reviewing your evidence before the end of the period, ensuring that you’ve uploaded the right documents and have sought a second opinion from experts at your compliance platform. You’ll also need to prepare a system description, which is a global explanation of your company, software and cybersecurity program; your auditor can help you with this.
Your auditor will now gather all the evidence from your compliance platform, review it, and potentially request additional evidence, for example:
- Any code changes into production during the audit period.
- Details on any regression testing that took place.
Once you’ve provided your auditor with additional evidence, they can complete your audit report.
The Finish Line: SOC 2 Compliance
If all goes well, you will now have a report with an “Unqualified” opinion, which means you have successfully proved that your company is SOC 2 compliant. If you have a “Qualified” opinion, that means you still have items to work on, but you’re on track to achieve your goals!
Remember, SOC 2 compliance is not a one-time event; you will need to continue working on your security practices to ensure smooth renewals of your audits.
Ticking Off Our SOC 2 Compliance Checklist
We’re so proud to have achieved our SOC 2 information security audit as it reflects our commitment to the highest standards of security, availability, processing integrity and confidentiality.
If you would like to see our SOC 2 report, request access here.
TL;DR
SOC 2 is a compliance framework developed by AICPA to mark a company’s commitment to robust security practices and meeting the standards.
Follow our SOC 2 compliance checklist to ensure a successful SOC 2 audit: choosing a robust compliance platform, assessing internal processes and identifying gaps, and deciding between SOC 1 vs. SOC 2.
The most common misconceptions of a SOC 2 audit are: it doesn’t absolve you from future security assessment, it’s not a permanent achievement, nor certification.











